NordStellar for Businesses: Proactive Cybersecurity in Action
What Is NordStellar and What Does It Offer?
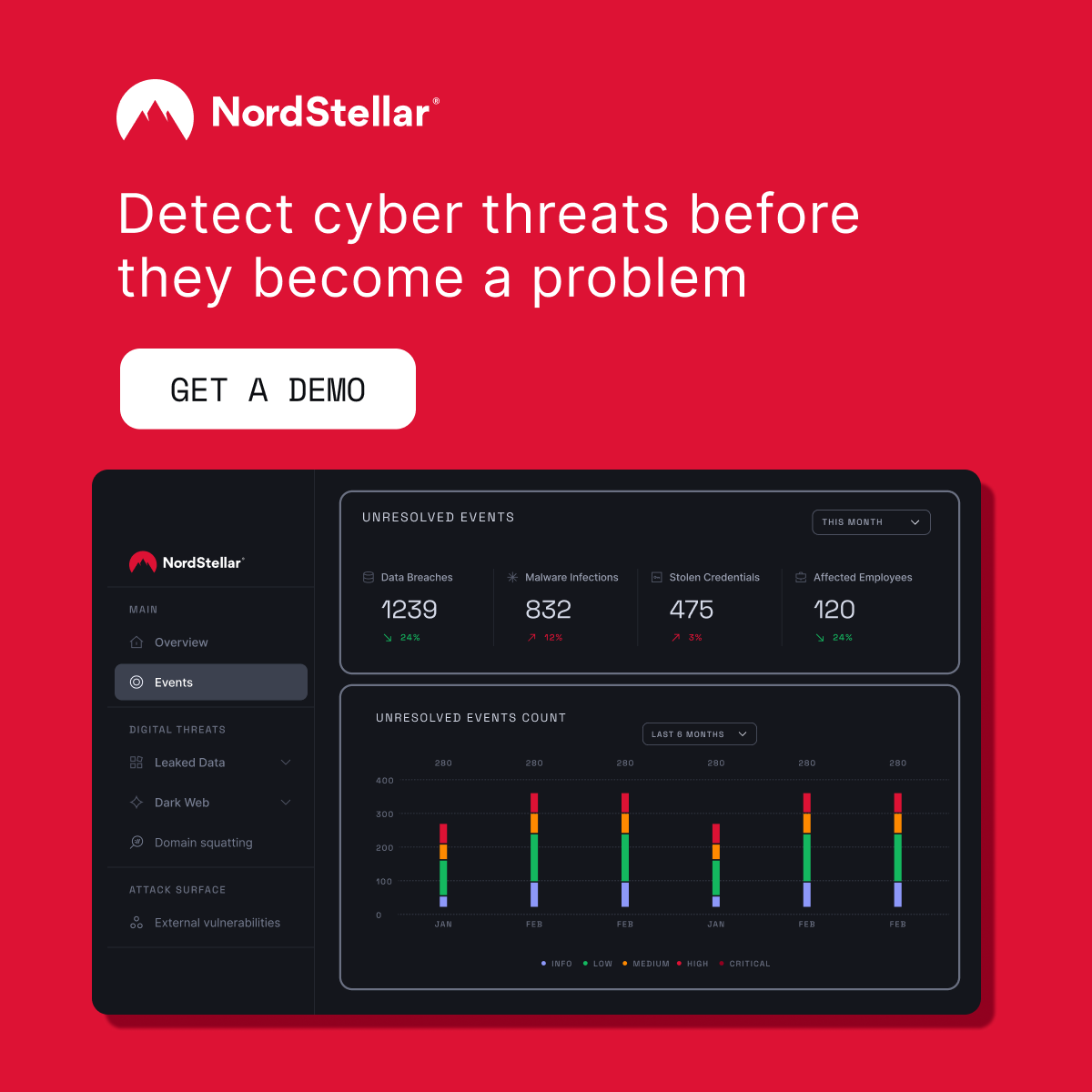
NordStellar is a centralized threat exposure management platform developed by Nord Security. It consolidates breach intelligence, dark web monitoring, and attack surface analysis into one streamlined dashboard.
Key features include:
- Data Breach Monitoring: Detect leaked employee or customer credentials in real time
- Dark Web Monitoring: Track brand mentions and threat chatter across forums, Telegram, and ransomware blogs
- Attack Surface Management: Map exposed infrastructure and detect vulnerabilities before they’re exploited
- Brand Protection: Prevent cybersquatting, impersonation, and unauthorized use of your company name
- Risk-Based Prioritization: Rank threats by business impact and likelihood of breach
- Real-Time Alerts: Get notified instantly when your data is exposed or targeted
NordStellar is designed to reduce detection time, cut technical debt, and empower security teams with actionable insights.
How NordStellar Differs from Traditional Security Tools
Unlike reactive antivirus or firewall solutions, NordStellar focuses on external visibility—what attackers see and target from the outside. It’s built to:
- Monitor over 40,000 threat sources including dark web forums and malware logs
- Analyze 90B+ leaked credentials and 50M+ malware records
- Provide instant alerts for breach events and brand misuse
- Help teams prioritize threats based on real-world attacker behavior
Traditional tools often miss early indicators of compromise. NordStellar catches them before they escalate.
Use Cases Across Teams and Roles
NordStellar is built to serve multiple layers of an organization:
- Executives gain visibility into risk posture and alignment with business goals
- Security Operations teams streamline detection and response workflows
- Threat Intelligence Analysts track adversaries and monitor external chatter
- IT Managers identify exposed assets and reduce attack surfaces
- Compliance Officers monitor data exposure to meet NIS2, DORA, and GDPR standards
Whether you’re defending a startup or a global enterprise, NordStellar adapts to your threat landscape.
Best Practices for Using NordStellar Effectively
To maximize NordStellar’s capabilities, consider the following:
- Connect your domain and assets to enable full-spectrum monitoring
- Set up keyword alerts for brand names, executive identities, and sensitive terms
- Review exposure reports weekly to track trends and emerging threats
- Integrate with SIEM or SOAR tools for automated response
- Use risk scoring to prioritize remediation efforts
- Schedule regular demos or training to keep teams aligned
- Monitor dark web mentions to stay ahead of targeted campaigns
- Audit your attack surface monthly to reduce entry points
These practices help transform NordStellar from a dashboard into a strategic defense layer.
Final Thoughts – Is NordStellar Worth It?
In a digital landscape where breaches are inevitable, visibility is power. NordStellar offers:
- Real-time threat detection
- External vulnerability scanning
- Dark web intelligence
- Brand protection
- Risk-based prioritization
For organizations seeking proactive, scalable, and privacy-respecting threat management, NordStellar is a serious contender.
Explore NordStellar and take control of your external threat exposure today.
Related Posts
Linux Mint: A Quiet Powerhouse for Everyday Computing
Linux Mint: Lightweight, Reliable, and Built for Everyday UseLinux Mint has earned a reputation as one of the most...
SSDs and NVMe Drives: Speed and Efficiency for Modern Systems
SSDs and NVMe Drives: Speed and Efficiency for Modern SystemsSolid-state drives (SSDs) and NVMe storage have...